(Only For N00bs not for advance users)
++++++++++++++++++++++++++
Method :- IIS Exploit.
Things Needed :- 1. IIS Vulnerable Sites.
2. Windows Operating System. (Windows XP, Windows 7, Windows
++++++++++++++++++++++++++
First of all you have to find a vulnerable IIS website. (Some will be provided for practice)
and just you have to follow my steps to perform this attack.
_______________________________________________
Sites For Practice :-
1 .www.advanceautomation.co.in
2. www.hljyhdc.com
3. www.268au.com
4. www.jsdtsx.com
5. www.lsmdly.com
6. www.itixiang.com
7. www.lvshi163.com
8. www.songspk.pk
9. www.infanziasantonio.com
10.www.msc-waldkappel-breitau.de
________________________________________________
******************************************
This technique is for Educational Purpose only and I am not responsible any harm done by you.
******************************************
________________________________________________
1. For Windows XP Users :-
STEP 1: Click on Start button and open “RUN”.
STEP 2: Now Type this in RUN
%WINDIR%EXPLORER.EXE ,::{20D04FE0-3AEA-1069-A2D8-08002B30309D}::{BDEADF00-C265-11d0-BCED-00A0C90AB50F}
Now A Folder named “Web Folders” will open.
STEP 3: Now “Right-Click” in the folder and Goto “New” and then “Web Folder“.
STEP 4: Now type the name of the Vulnerable site in this. e.g.” http://autoqingdao.com/” and click “Next“.
STEP 5: Now Click on “Finish“
STEP 6: Now the folder will appear. You can open it and put any deface page or anything.
STEP 7: I put text file in that folder. Named “securityalert.txt” (you can put a shell or HTML file also). If the file appear in the folder then the Hack is successful but if it don’t then the site is not Vulnerable.
Now to view the uploaded site i will go to “http://autoqingdao.com/securityalert.txt”
In your case it will be ” www.[sitename].com/[file name that you uploaded] “
_______________________________________________
For Windows 7 Users :-
1. Open My Computer.
2. Right Click in the white space and select "Add a network location"
3. A Window will pop up
3. Click Next
4. Double Click "Choose A custom Network"
5. Add the vulnerable IIS website !
in my case i am using
http://admats.concerts.com/
6. Click Next! Then wait a little second !
7. Then a Web Folder will open
8. Upload your Deface page or Shell
Finish!
__________________________________________
For Windows 8 Steps are same as Windows 7... Enjoy.... xD
Method :- IIS Exploit.
Things Needed :- 1. IIS Vulnerable Sites.
2. Windows Operating System. (Windows XP, Windows 7, Windows
++++++++++++++++++++++++++
First of all you have to find a vulnerable IIS website. (Some will be provided for practice)
and just you have to follow my steps to perform this attack.
_______________________________________________
Sites For Practice :-
1 .www.advanceautomation.co.in
2. www.hljyhdc.com
3. www.268au.com
4. www.jsdtsx.com
5. www.lsmdly.com
6. www.itixiang.com
7. www.lvshi163.com
8. www.songspk.pk
9. www.infanziasantonio.com
10.www.msc-waldkappel-breitau.de
________________________________________________
******************************************
This technique is for Educational Purpose only and I am not responsible any harm done by you.
******************************************
________________________________________________
1. For Windows XP Users :-
STEP 1: Click on Start button and open “RUN”.
STEP 2: Now Type this in RUN
%WINDIR%EXPLORER.EXE ,::{20D04FE0-3AEA-1069-A2D8-08002B30309D}::{BDEADF00-C265-11d0-BCED-00A0C90AB50F}
Now A Folder named “Web Folders” will open.
STEP 3: Now “Right-Click” in the folder and Goto “New” and then “Web Folder“.
STEP 4: Now type the name of the Vulnerable site in this. e.g.” http://autoqingdao.com/” and click “Next“.
STEP 5: Now Click on “Finish“
STEP 6: Now the folder will appear. You can open it and put any deface page or anything.
STEP 7: I put text file in that folder. Named “securityalert.txt” (you can put a shell or HTML file also). If the file appear in the folder then the Hack is successful but if it don’t then the site is not Vulnerable.
Now to view the uploaded site i will go to “http://autoqingdao.com/securityalert.txt”
In your case it will be ” www.[sitename].com/[file name that you uploaded] “
_______________________________________________
For Windows 7 Users :-
1. Open My Computer.
2. Right Click in the white space and select "Add a network location"
3. A Window will pop up
3. Click Next
4. Double Click "Choose A custom Network"
5. Add the vulnerable IIS website !
in my case i am using
http://admats.concerts.com/
6. Click Next! Then wait a little second !
7. Then a Web Folder will open
8. Upload your Deface page or Shell
Finish!
__________________________________________
For Windows 8 Steps are same as Windows 7... Enjoy.... xD




















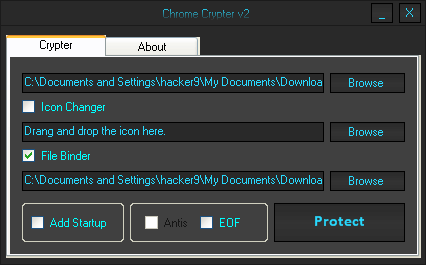
 Download:
Download: 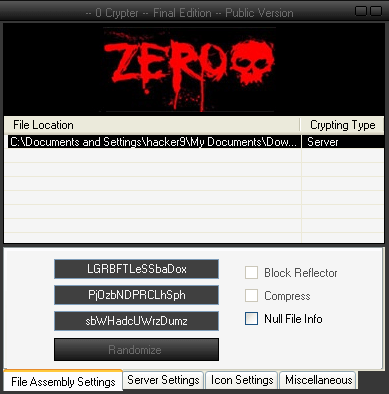

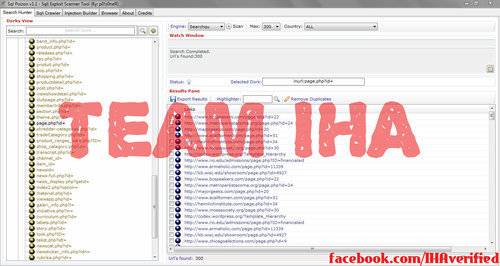


Mologogo
http://www.mologogo.com/
Buddyway
http://www.buddyway.com/
InstaMapper
http://www.instamapper.com/
LocateA.net
http://www.locatea.net/